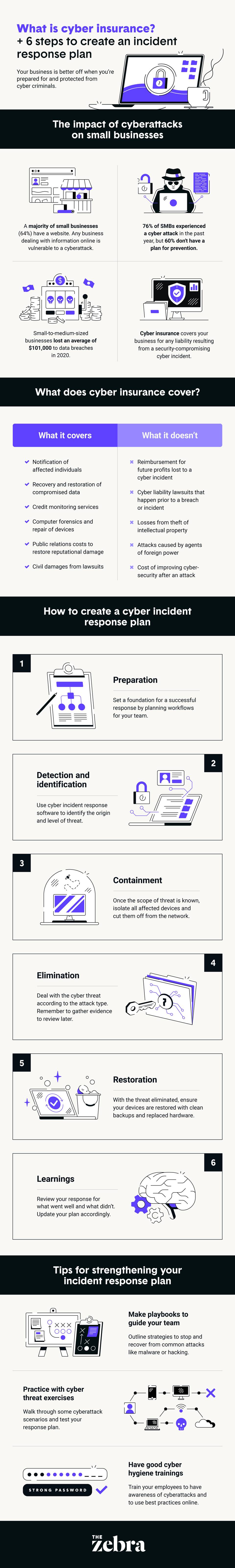
How to create a cyber incident response plan
Even if your business is covered for cyber liability, it’s smart to have procedures in place for employees in case a cyberattack happens. The best cybersecurity practice is to have a cyber incident response plan. This type of plan will provide guidance for containing the incident, as well as protocol for recovering devices and repairing damage. Additionally, having a good plan in place will help strengthen your business’s cybersecurity and help lower your insurance premiums.
To help you understand the basics of putting together a plan, read up on the six stages of incident response plans outlined below.
1. Prepare your business
The first stage in an incident response plan is preparation, which provides the foundation for all other stages hereafter. In this stage, you’ll want to outline your team’s workflows in response to an incident. This includes identifying exactly who is responsible for specific actions that must be performed to remedy the situation. The plan should include, but is not limited to, the following:
- Who is responsible for locating where and when a breach or attack originated
- Guidelines for triaging the event based on your security capabilities and what types of incidents require third party support
- A list of vetted vendors to provide incident response support
- Workflows for how other teams like legal, PR and customer service will respond
- An established hierarchy of command for the incident with approval from top stakeholders
- Procedures for storing important credentials in a centralized location
2. Identify the event
With this preparation in place, if an incident occurs, you’ll have a guideline to begin diagnosing the problem. This typically involves specialized personnel and cyber incident response software to begin documenting information that will help identify the origin and level of threat.
At this stage, the type, severity and scope of the event should be determined and stored in case of legal action later. It’s important to be proactive about detection and use technology like antivirus software and programs that can detect malware.
3. Contain the incident
After successfully identifying the event and the scope of the threat, you can start containing any compromised devices and isolating them from the network to prevent any further progression of an attack. Depending on the incident, it’s smart to have both short-term and long-term containment strategies prepared to respond accordingly.
4. Eliminate the threat
Once containment of the threat is achieved, you and your team can work on eliminating it. This will look different depending on the attack. For example, malware attacks will need to be disarmed and ransomware will need decryption. You should continue to gather evidence in this stage and preserve details for future analysis. It’s also good practice to patch systems, replace hardware and update networks and firewalls as needed.
5. Restore systems, services and processes
After the threat has been eliminated, your business will need to restore systems and return to regular work. To do this, you’ll need to have clean data backups and any affected devices should be rebuilt and recovered. Additionally, updating relevant credentials and logins after an incident will prevent compromised information from being used in the future. Continue to monitor your network and systems in case of further issues.
6. Learn and adapt for the future
Once normal business is restored, it’s important to reflect on the incident and your response plan. You can accomplish this in a post-incident review (PIR) meeting, which will involve all relevant personnel from the response. Discuss what worked well and what could be improved and implement any improvements in your incident response plan moving forward.